
A cyberattack on the service provider RTX caused Chaos at Airports
One weak link in the supplychain can trigger a cascade of disruptions that shot down airport operations
The failure during check-in at BER Airport and other European hubs, caused by a cyberattack on the service provider RTX, highlights the vulnerability of modern software and cloud supply chains. This incident demonstrates how a weak link can cause a chain reaction of disruptions, significantly impacting airport operations overall. Therefore, companies must expand their cyber risk analysis beyond their own infrastructure to include the entire supply chain and all external service
Why is cybersecurity so important in the supply chain?
Increasing digitalization has transformed supply chains into highly networked ecosystems. As the case of BER airport shows, a weak point in a cloud service, cybersecurity service, or IT service provider can be an open door for attacks on your own company. Such vulnerabilities can lead to business interruptions, data loss, and a massive loss of trust, resulting not only in financial losses but also long-term damage to your reputation. Growing regulatory requirements, such as the NIS2 Directive, are forcing companies in the KRITIS sector (critical infrastructures) to systematically check their supply chains for cyber risks and take appropriate protective measures.
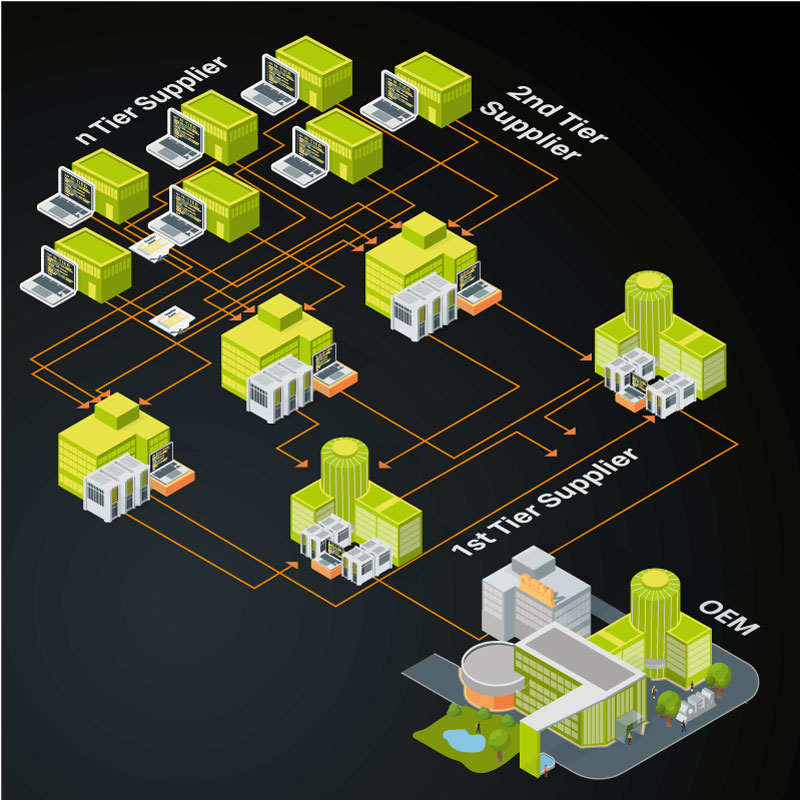
In-depth aspects of cybersecurity in the supply chain
The cyber attack on BER Airport show: The complexity of the modern supply chain requires a holistic approach. Companies are not only responsible for their own security, but also for that of their partners. This means that they need to know and understand the software bill of materials (SBOM) of all components used. An SBOM is like an ingredient list for software: it lists all the open-source and proprietary components that make up an application. Without this knowledge, it is impossible to identify vulnerabilities that may lurk in these complex components.
Another crucial element is third-party risk management (TPRM). Many companies rely on dozens or even hundreds of external providers, from cloud services to specialized software developers. Each of these partners represents a potential risk. Comprehensive TPRM involves regularly reviewing these partners' security measures, ensuring compliance with contractual obligations, monitoring their own cybersecurity, and requiring them to report cybersecurity incidents.
The added value of asvin.io: Risk By Context
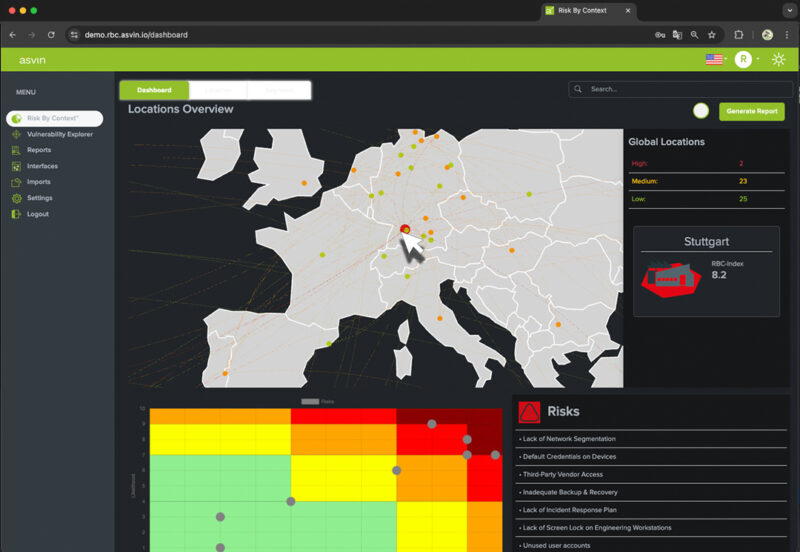
This is where asvin's cybersecurity solutions and services come in. Our Risk By Context™ platform is specifically designed to address the complexity of supply chain cybersecurity. It goes far beyond simple risk assessment, offering dynamic and contextual analysis that prioritizes risks and dependencies in real time.
Instead of simply presenting a list of potential cyber risks posed by suppliers, Risk By Context™ analyzes which supplier poses the greatest real risk to business operations. It does this by linking threat data and your own BCM with the specific context of the supply chain. Take, for example, a software component with a known security vulnerability. Risk By Context not only assesses the severity of the vulnerability, but also where and how that component is used in the supply chain. This contextual assessment enables companies to deploy their limited resources where they add the most value to resilience.
Our platform also helps companies ensure compliance with regulations such as NIS2 by providing the necessary transparency in the supply chain and documenting risk assessments.
What needs to be done?
To protect themselves effectively, companies need to take the following steps:
- Risk assessment: Conduct regular, in-depth assessments of the cyber risks of all partners in your supply chain.
With asvin Risk By Context, you have the optimal tool at your disposal to perform
these assessments dynamically and contextually. - Contract drafting: Integrate clear cybersecurity requirements and liability clauses into contracts with service providers.
- Technology: Use modern technologies to proactively monitor IT security throughout your supply chain. The cyber risk analysis platform from asvin.io is an indispensable tool that helps you identify and prioritize vulnerabilities.
It is high time to learn from the mistakes of others: prevention is the best protection. Understand cybersecurity as an integral part of your supply chain strategy. This is the only way to ensure that your company remains operational in the event of an attack and retains the trust of your customers.






