Why is a comprehensive cyber risk management solution essential?
Companies in manufacturing and critical infrastructure face complex cybersecurity challenges.
Risk prevention requires significant investment, but it’s crucial to allocate resources effectively.
Risk by Context™ provides a complete overview transcending departmental boundaries.
Our methods enable quick decision-making, timely responses to threats, and cost-effective allocation of resources for maximum value from cybersecurity investments.
We tackle your industry’s challenges
Discover how our solutions provide security and protection for your business and valuable assets. Our services include not only risk management, but also Device Update Management, Enterprise Engineering Support, Compliance Regulatory Readiness Consulting, and seamless deployment services.
Think of cyber risks as part of your general business risks
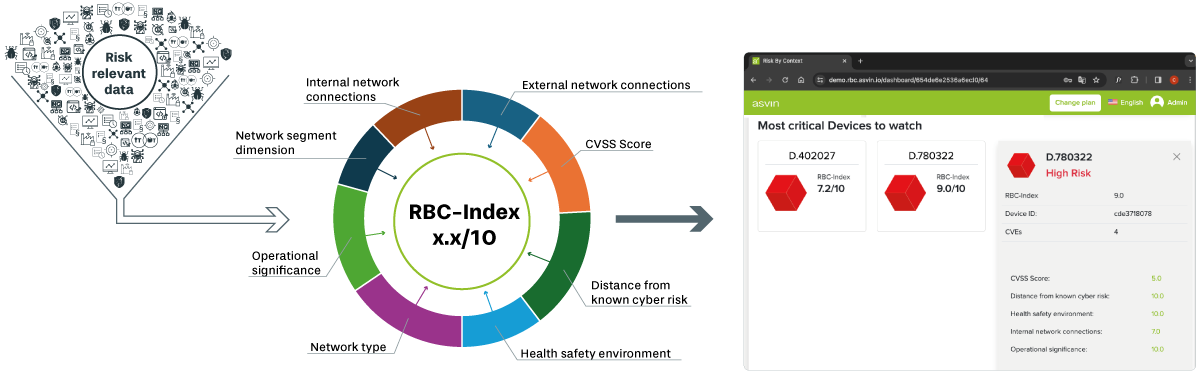
Our AI-powered solution utilizes a variety of existing cybersecurity metrics, network and asset data, as well as other crucial business data to create the RBC Index. By analyzing your digital infrastructure and its dependencies, you can accurately evaluate the risks associated with your business and make informed decisions to safeguard against potential threats.
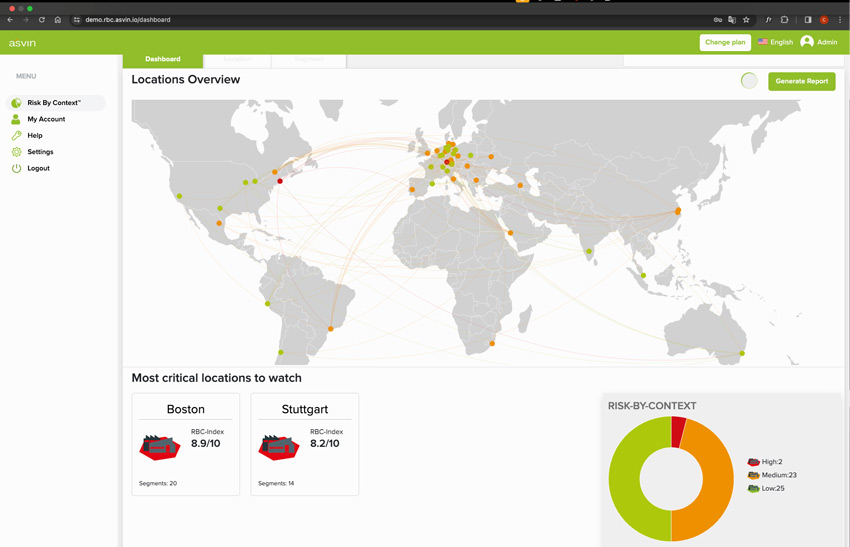
Get the big picture in seconds
The graph visualization displays the risk level of every location, along with their interconnections.
Your most critical locations to watch are displayed on info cards for quick access to deeper levels.
Explore further and discover where to head.
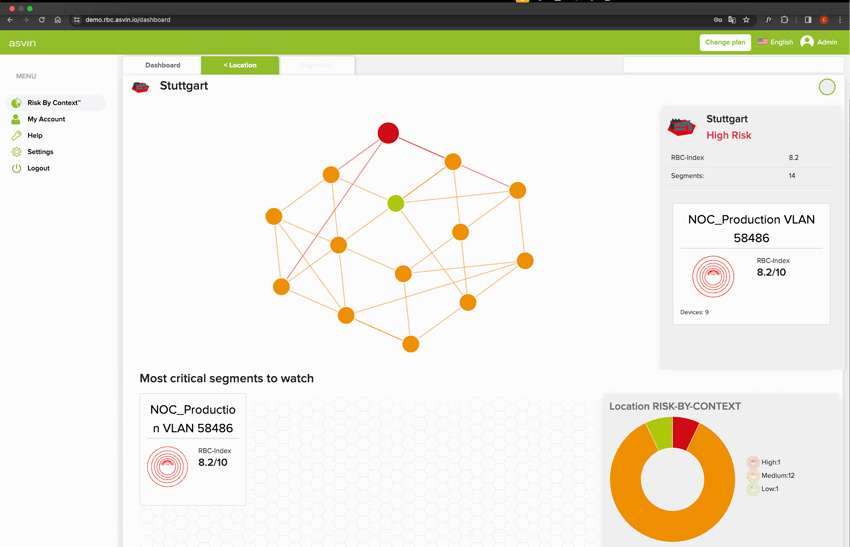
At the location level, you can easily view all network segments and their risk status, so the responsible parties can know what requires attention.
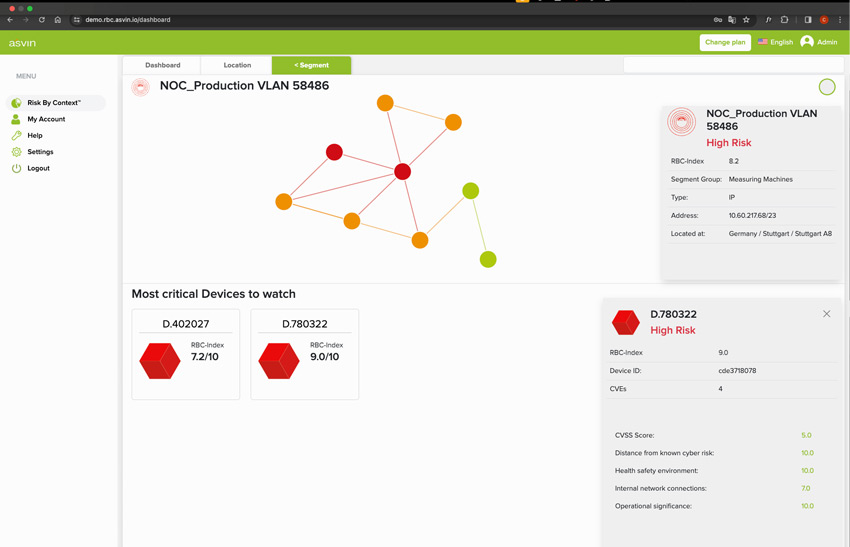
Go into detail and find the root cause
At the segment level, you get detailed insights into each individual asset, their connections to each other, and the rating of the individual context elements. These insights are used to create the Risk by Context Index.