Automotive
increase cybersecurity, keep innovation
We are aware of the complex cybersecurity challenges facing modern cars
As the responsible person for cybersecurity in the automotive industry, you play a critical role in protecting your organization’s networks and systems against cyber threats.
However, with modern cars’ numerous electronic control units (ECUs) and complex networks, ensuring adequate protection can be a challenge.
Our cybersecurity experts at asvin specialize in helping car manufacturers, suppliers, and regulators navigate the complexities of modern car systems and mitigate the supply chain risks posed by third-party vendors and suppliers. Let us help you ensure regulatory compliance for Cybersecurity Management (CSMS) and Secure Update Management (SUMS) while adequately protecting all the different systems and components against cyber threats.
Contact us today to learn more.
asvin`s Cybersecurity Tools for Automotive

Eagle Eye
Manage, analyze and prioritize threats and risks according to the risk-by-context principle

Ant Street
Simply manage your
Assets/Fleet and
OTA Updates

Paw Print

Track Hound
Track the History of your CI/CD Pipelines along the Software Supplychain

Regulatory compliance
for type approval
We offer cutting-edge cybersecurity solutions that support automotive manufacturers in fulfilling regulatory compliance requirements for type approval. Our solutions comply with UNECE WP.29, ISO26262, ISO/SAE 21434, and R195, ensuring that our customers meet the highest standards of cybersecurity.
Our solutions unique Context based Riskanalyses allows companies to identify and prioritize vulnerabilities based on their level of risk . We also offer Over-The-Air (OTA) updates that help automotive manufacturers maintain the security and functionality of their vehicles’ software
As automotive manufacturers you can have peace of mind that your vehicles’ software is secure and compliant with regulatory requirements. Our solutions are customizable, real-time monitored, and risk-based, ensuring that our customers can detect and respond to security threats quickly.
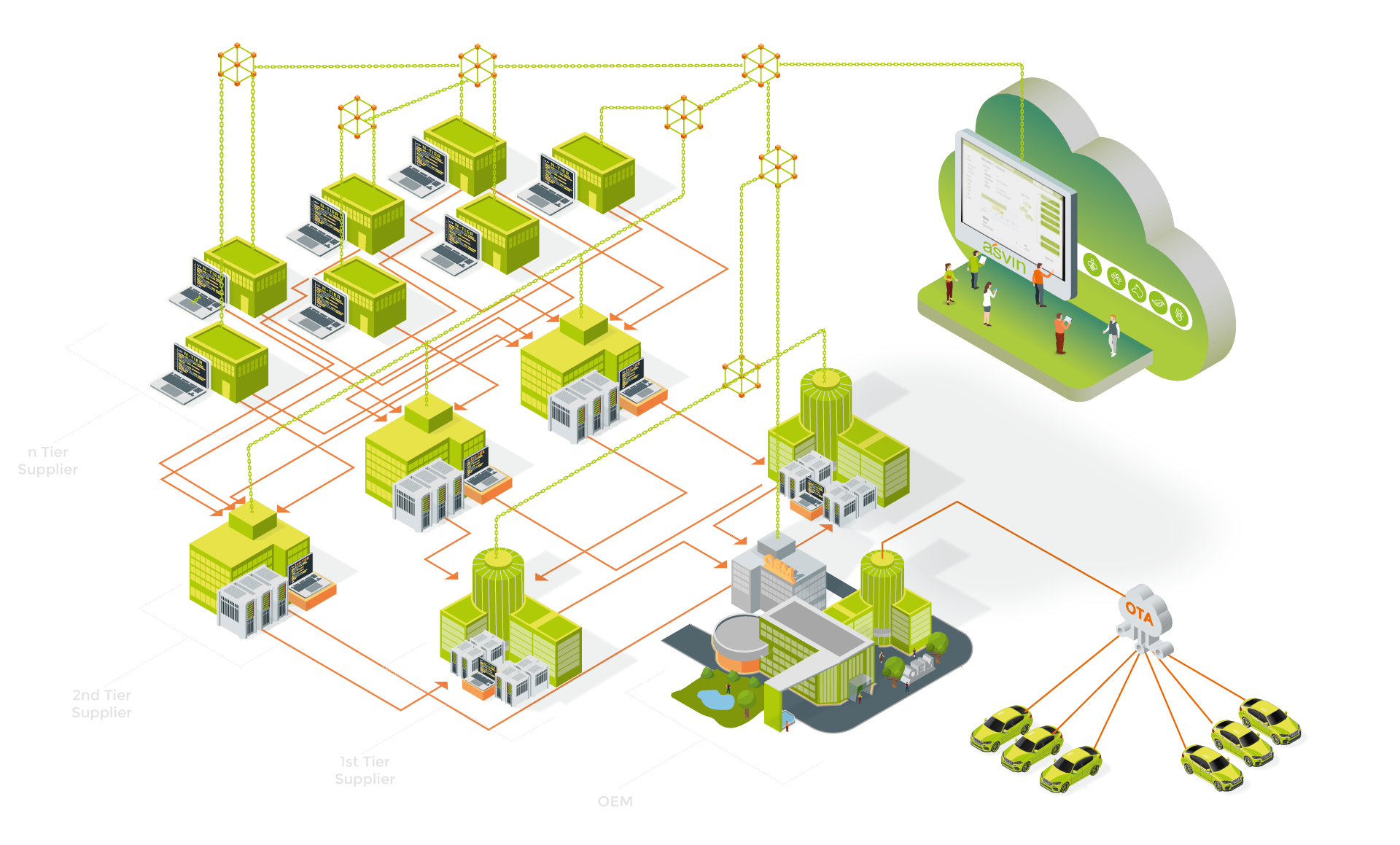
Software Supply Chain Trust and Security
Our cutting-edge tools offer a complete new approach to software-defined vehicle lifecycle management and automotive software supply chains. With our innovative technology, you can manage the increasing complexity of software supply and supplier dependencies, monitor risks, and speed up the flow of trustful information related to software from n-tier suppliers to your specific vehicle.
Track and trace the integrity and provenance of software supply chains: from development towards CI/CD pipelines, OTA update distribution towards operation on vehicles.
Our solution also allows you to instantly retrieve software-related meta-information from a distributed ledger network. This eliminates the need to downstream requests for information and wait for upstream reports from suppliers. All software-related information is collected in the network, and stakeholders can commit their information for SBoM and software integrity to the decentralized asvin ledger network architecture.
Embrace a more secure and streamlined approach with asvin.io. Enhance your cybersecurity and trust in software supply chains today!
DECENTRALIZED SOURCING
Transparency of software sourcing in supplier networks, traceably of software from n-tier supplier to IoT asset (e.g., vehicle)
The automotive software supply chain is characteristically convoluted because of its multi-tier OEM hierarchy. asvin facilitates a decentralized solution powered by distributed ledger technology (DLT) tosecure automotive software supply chain. It incorporates cryptographic algorithms, DLT, and web application tools to trace the track of software supply chain. Additionally, it helps to establish software provenance, unbroken chain of trust and transparency. At each stage of the software supply chain the digital signature of the software is calculated and stored with other critical metadata on a distributed ledger.
RECALL MANAGEMENT
Dare to do more! What if you used recall management not only as a tool for brand loyalty or to ensure regulatory compliance? But also to position yourself as a software OTA champion that operates its entire infrastructure, including vehicles and services, securely and updateably over the air. Trustworthy and service-proof.
asvin`s cybersecurity management system creates an immutable and traceable trust protocol based on DLT that documents the entire software supply chain and the lifecycle of vehicles.
Tools, Main-Features and Services

- Distributed Software Bill of Materials generation (D-SBoM)
- Resilient infrastructure for providing SBOMs due decentralized ledgers
- Immutable storage of information, protected from manipulation by cyberattacks

- Update and Patch Distribution
- Device Management
- API interface to OTA platforms

- Software Supply Chain License and Version Management
- Operation tracking and documentation in distributed ledger (DLT)
- Software Supply Chain Monitoring
- Supplier Risk Analytics

LIABILITY MANAGEMENT

Respond calmly to the threat of liability shifting from the end customer to the manufacturer due to autonomous driving. Lawyers warn that users of an automation function while driving are not liable as vehicle drivers under Section 18/1 of the Road Traffic Act (StVG)? You will be prepared for this in the future. Simply step out of the liability risk.
With asvin, you perform software updates at predefined times or as ad-hoc emergency patches in the event of a safety or liability incident. This not only makes you safe from the cadi. You can simply avoid it.
Tools, Main-Features and Services

- Software Supply Chain License and Version Management
- Operation tracking and documentation in distributed ledger (DLT)
- Software Supply Chain Monitoring
- Supplier Risk Analytics

- IT/OT/IoT Threat Landscape Modeling
- Supply Chain Risk Modling
- Risk Mitigation
- SUMS Strategy
- CSMS Strategy
- ISMS Strategy
- Cybersecurity Mesh Architectures
- Cybersecurity Graph Analytics
- Lifecycle Security Systems
SECURITY/SAFETY RISK MITIGATION
Minimizing cybersecurity risks becomes a competitive advantage. Demonstrate your risk readiness to your customers! And take your suppliers with you at the same time. You achieve this through active information exchange between all peers in the software supply chain. End-to-end and purpose-built visibility of relevant data turns all stakeholders into risk checkers that react quickly to threats within the automotive software supply chain. And faster than hackers suspect.
Proactive SCRM strategies, created using asvin tools, identify and assess potential risks before they occur. And ensure contingency plans are prepared and significant losses are prevented.
Tools, Main-Features and Services

- Software Supply Chain License and Version Management
- Operation tracking and documentation in distributed ledger (DLT)
- Software Supply Chain Monitoring
- Supplier Risk Analytics

- Device Attack Monitoring
- Integrity Monitoring
- Security Monitoring

- Distributed Software Bill of Materials generation (D-SBoM)
- Resilient infrastructure for providing SBOMs due decentralized ledgers
- Immutable storage of information, protected from manipulation by cyberattacks

- IT/OT/IoT Threat Landscape Modeling
- Supply Chain Risk Modling
- Risk Mitigation
- SUMS Strategy
- CSMS Strategy
- ISMS Strategy
- Cybersecurity Mesh Architectures
- Cybersecurity Graph Analytics
- Lifecycle Security Systems
OVER THE AIR UPDATE MANAGEMENT
No partially or fully autonomous driving without software updates. Now that the proportion of connected vehicles is increasing and the EU is also taking regulatory action (“Resilience Act” from mid-September 2022), the automotive and industry sectors are experiencing an unprecedented growth spurt. But only if all stakeholders consistently implement the new and necessary safety requirements. And if they implement the regulations according to UNECE WP 29 R 155; R156; R157), ISO/SAE 21434 as well as the upcoming ISO 24089 standard. You can do that now. With us.
asvin cybersecurity management provides a decentralized general ledger to store all actions performed in the software supply chain. From provisioning, testing, and OTA distribution to installation, execution, and updating in vehicles in the field.
Tools, Main-Features and Services

- Manage, Update and Control Device Fleets

- Update and Patch Distribution
- Device Management
- API interface to OTA platforms

- IT/OT/IoT Threat Landscape Modeling
- Supply Chain Risk Modling
- Risk Mitigation
- SUMS Strategy
- CSMS Strategy
- ISMS Strategy
- Cybersecurity Mesh Architectures
- Cybersecurity Graph Analytics
- Lifecycle Security Systems