Cyberattacks continue to rise. Regulatory requirements like NIS2 increase expectations for transparency, responsiveness, and accountability.
For security leaders, this means more sources, more data, more reporting obligations – but not automatically more clarity in CTI reporting. Many organizations already have Cyber Threat Intelligence (CTI). Yet, the data is often scattered, inconsistent, and only usable with significant manual effort.
What’s missing is a reliable path from threat data to decision-ready reports.
Why Traditional CTI Reporting Falls Short
CTI reporting transforms threat intelligence into actionable insights for different roles.
It’s not the data volume that matters – it’s the right context for decision-makers.
Without Context, CTI Remains Abstract
A single indicator does not provide a basis for decisions.
Executives need to assess:
- whether the organization is impacted
- which systems are a priority
- potential business impacts
- necessary actions
Only then does threat data become actionable intelligence.
Different Organizations, Different Needs
Small teams need rapid deployment without long integration phases. Large SOCs require deep customization and control over data flows.
Modern platforms accommodate both realities – from immediately usable cloud services to fully integrated on-premise deployments.
Success depends not on location, but on how quickly information translates into action.

From Noise to Clarity
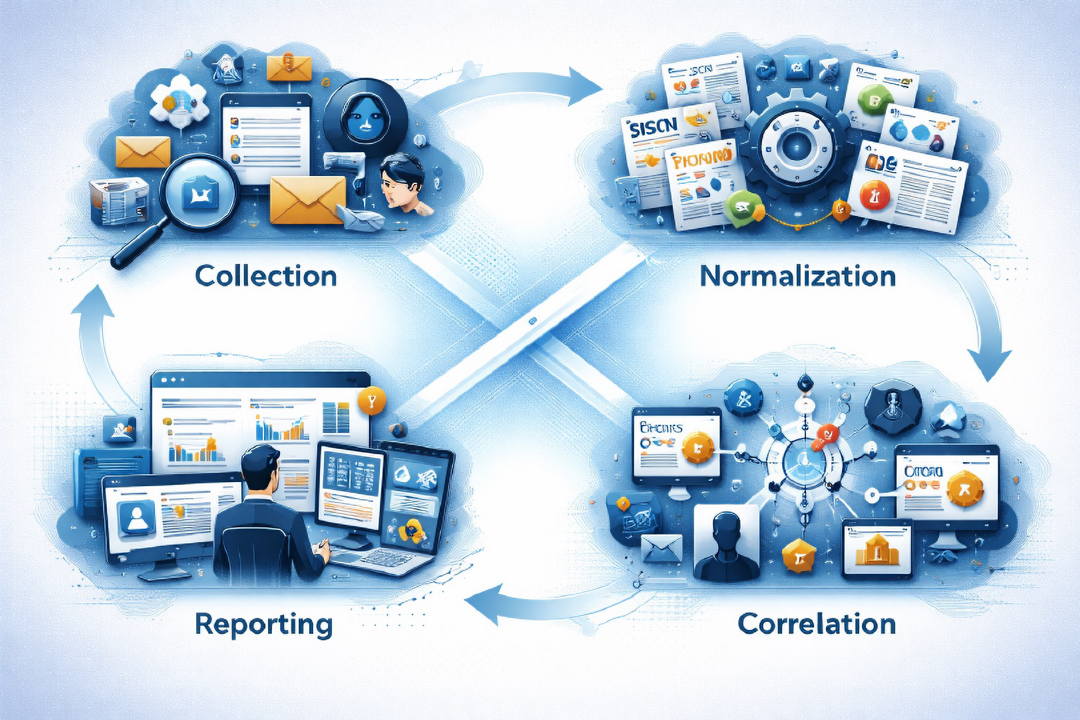
asvin automates the processing of cyber threat intelligence (CTI) - normalizing data sources, correlating information, and providing it in the right context for informed security decisions.
So that reports not only read, but also used.