asvin’s CTI layer enables large organizations to systematically convert unstructured threat data into structured, role-specific intelligence — automatically, AI-supported, and scalable across departments.
Integrated into the Risk by Context™ platform, it ensures that CISOs, SOC teams, and compliance stakeholders gain a consistent, prioritized threat landscape — aligned with operational responsibility, business relevance, and regulatory requirements such as UN R155, NIS2, and the Cyber Resilience Act.
The result: faster incident response, improved coordination, and documented readiness — across all business units.
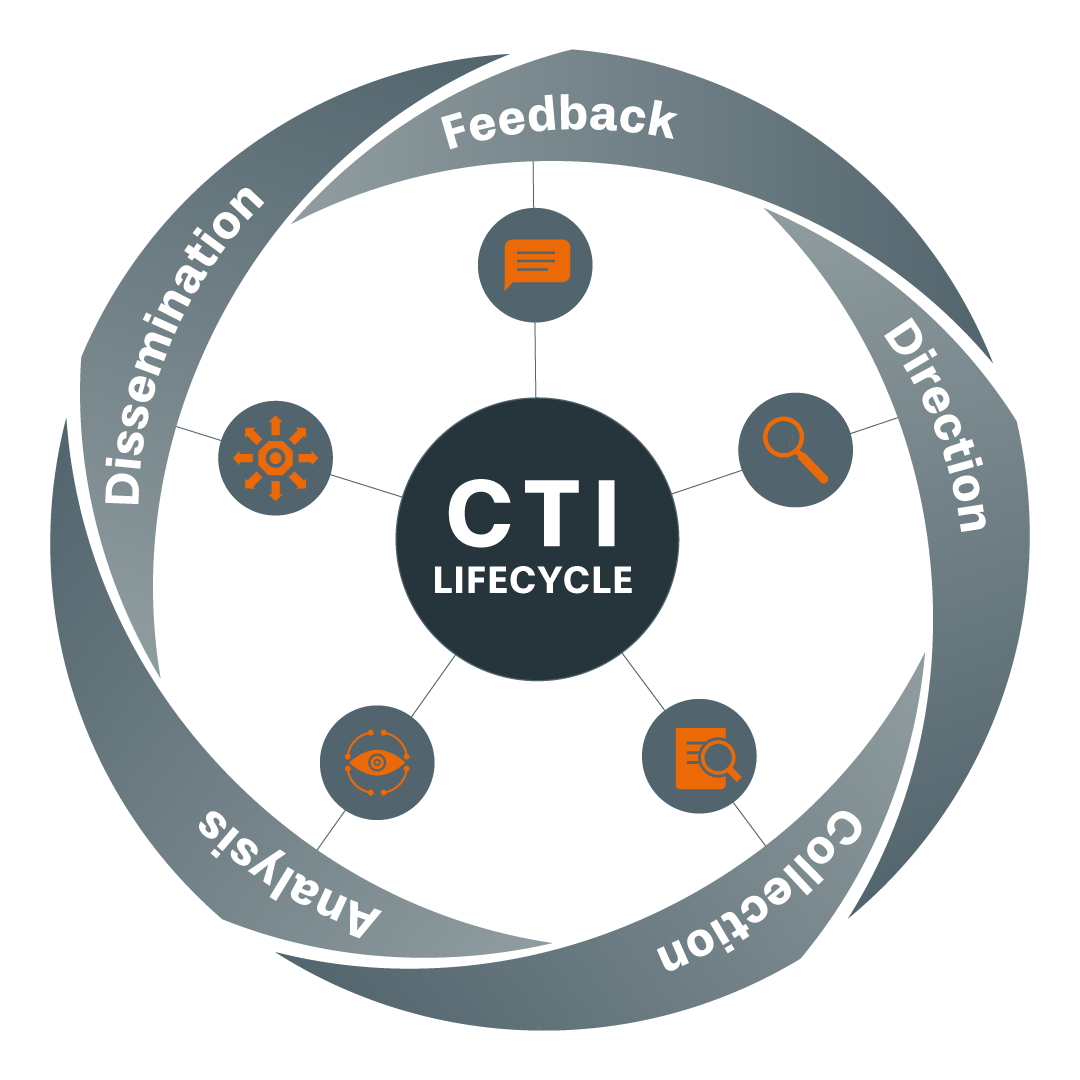
Cyber Threat Intelligence today is fragmented, manual, and out of context.
Organizations face an overwhelming volume of unstructured data. Threat reports are disconnected from business realities and differ across departments. As a result, CISOs and SOC teams struggle to act consistently, fast, and aligned with real risk.
We change that — by turning noise into clarity.
The Solution – asvin’s CTI Layer
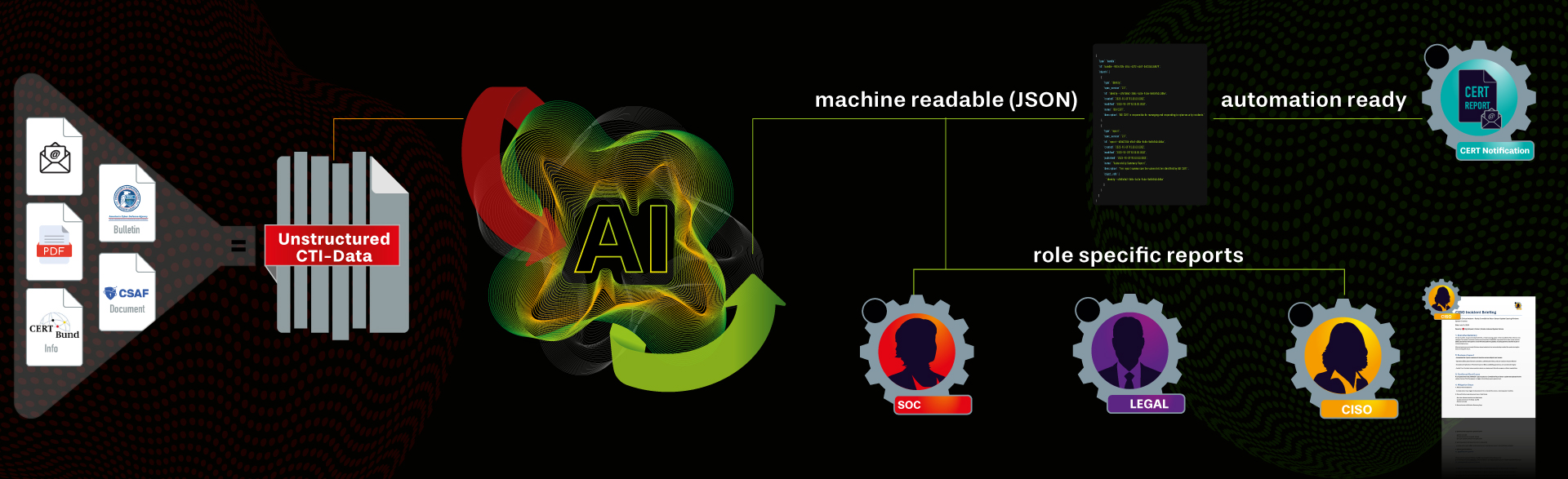
asvin AI Agents convert any CTI Note from any given format into standardized format for customized and role based reports
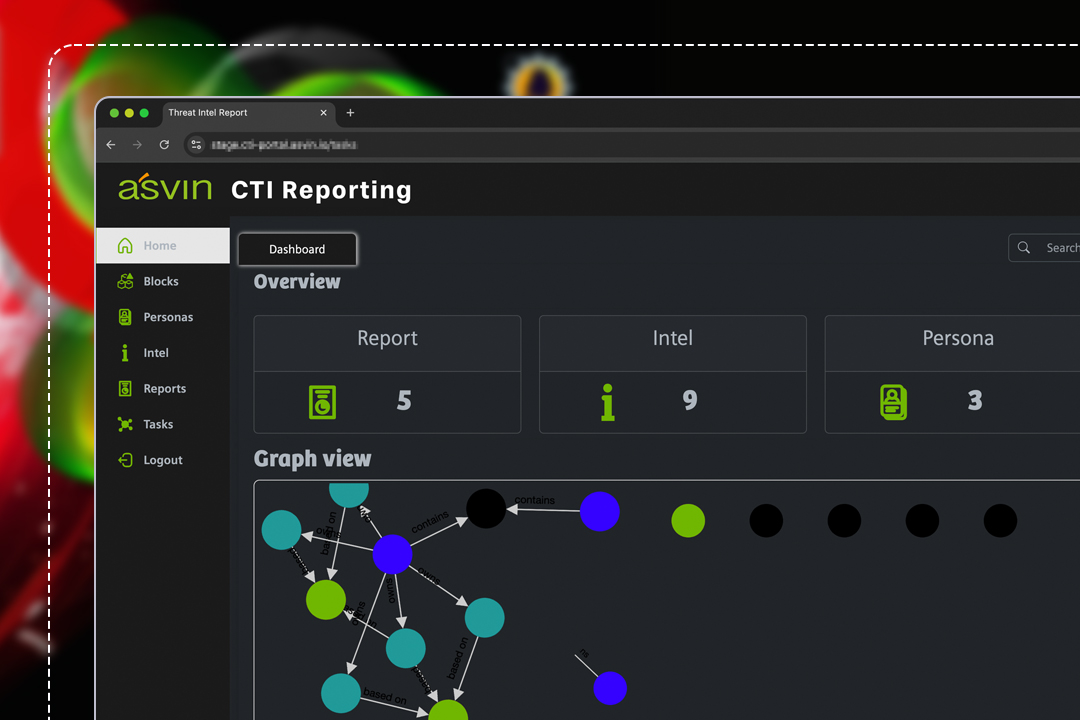
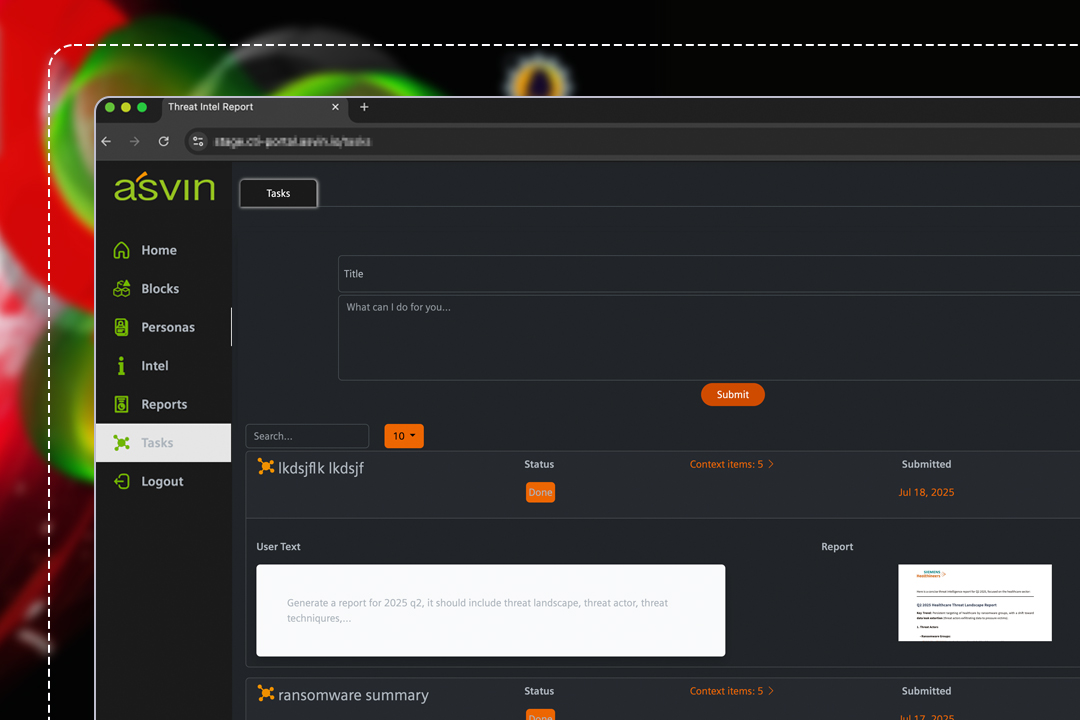
CTI Dashboard at a glance
The Cyber Threat Intelligence layer from asvin transforms scattered cyber threat data into structured, actionable intelligence — tailored to your organization, and to each stakeholder’s role.
Part of the Risk by Context™ platform, it automatically ingests data from multiple sources, enriches it via AI, and delivers human- and machine-readable intelligence (PDF, JSON, API).
Instead of disconnected reports, you get unified, contextualized insights — built for action, not just analysis.
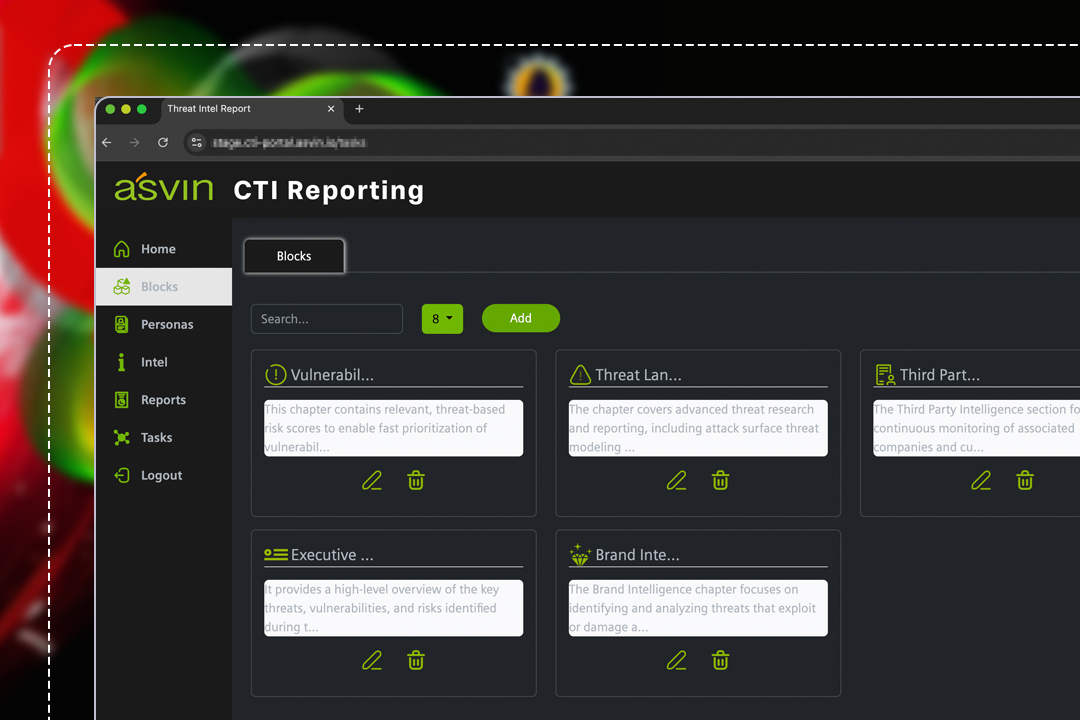
CTI reporting – A look at the demo view