Why is scalable IOT update lifecycle management so important?
Navigating the complex world of legal requirements and industry standards (CRA, NIS 2, IEC 62443, ISO 27001), industrial companies face challenges in managing IoT device fleets. Balancing device maintenance costs and cybersecurity risks becomes crucial as fleets grow and operational lifetimes extend.
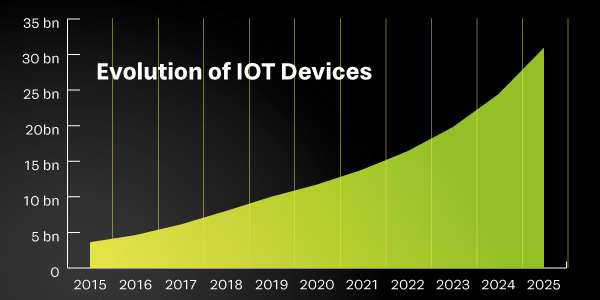
The number of IoT devices has long overtaken the number of non-IoT devices. There are already around 17 billion connected IoT devices today. This number is expected to almost double by 2030.
Device Security Booster™ supports operators to seamlessly handle the IoT update management over the entire product lifecycle, despite rapidly growing IOT fleets.
What are the benefits of using Device Security Booster™ for an organization?
Device Security Booster enables your IoT Software Update Management (SUM) to meet regulatory requirements for implementing security by design on connected devices, managing cybersecurity, and delivering patches and updates. Maintain the resilience of your connected devices throughout the entire product lifecycle.
We tackle your industry’s challenges
Discover how our solutions provide security and protection for your business and valuable assets. Our services include not only Device Update Lifecycle Management, but also risk management, Enterprise Engineering Support, Compliance Regulatory Readiness Consulting, and seamless deployment services.
Gain full control of over-the-air configuration and IoT update management.
Easy-to-understand dashboards guide you to easily implement and operate a cybersecurity management system for IoT/OT device fleets.
Device Security Booster™ supports OTA over-the-air updates for IoT-specific RF protocols such as LoRaWAN, 5G, NB-IoT, WLAN and LAN, Lightweight M2M, to name a few.

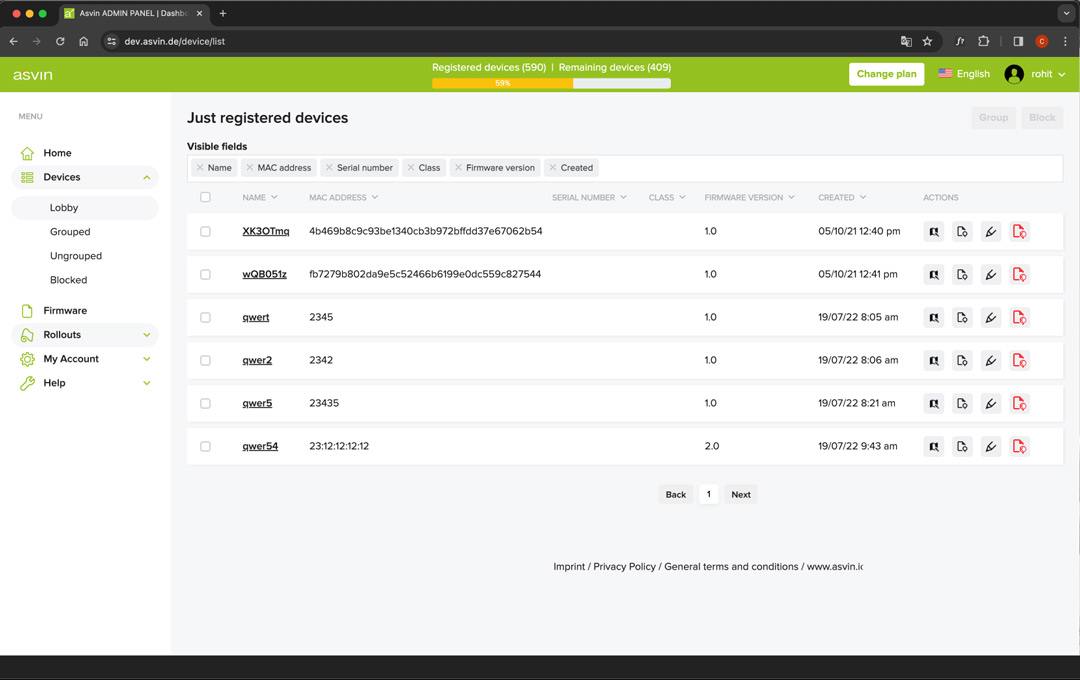
Device Management
In order to keep track of even large IOT fleets, all connected devices are organized in groups.
The health status of the devices is displayed in real time and you can block devices at any time if something appears suspicious.
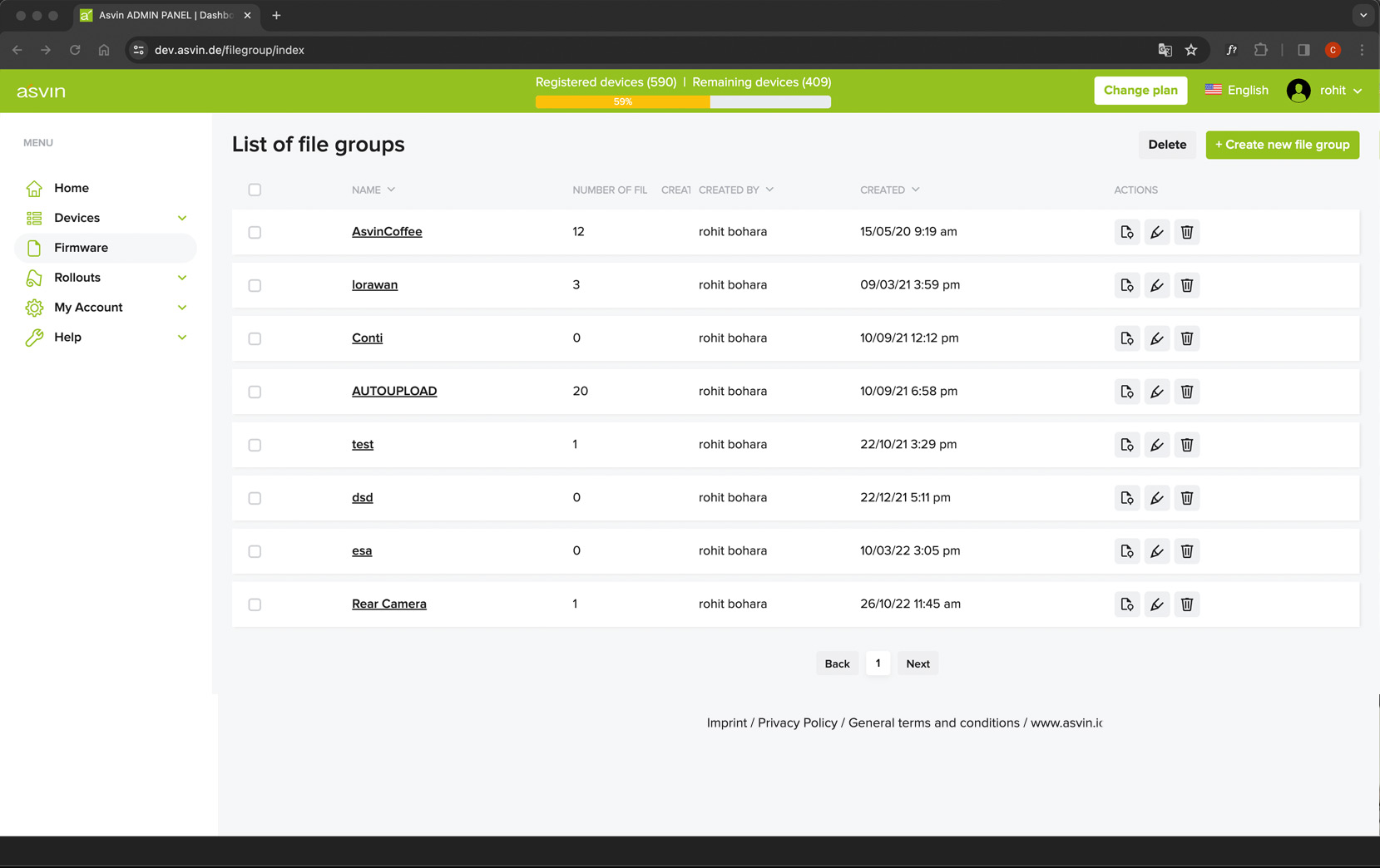
Firmware Management
All firmware files are scanned, organized and stored on peer-2-peer file server.
Rollout Management
Over the Air software update
can be distributed for registered device.