With the advancement of software-defined vehicles (SDV) and its related connected vehicles the Cybersecurity attack surface of vehicles, its IT backend and the entire supply chain is increasing.
Remote cyberattacks outnumber physical attacks by 85%, with 40% of those attacks targeting back-end servers used to support connected vehicles and related infrastructure. Perhaps more alarming, cyberattacks have increased 225% in the past three years, in large part because of all the connected electronics. Research firms estimates losses for the global auto industry could reach $505 billion by 2024.
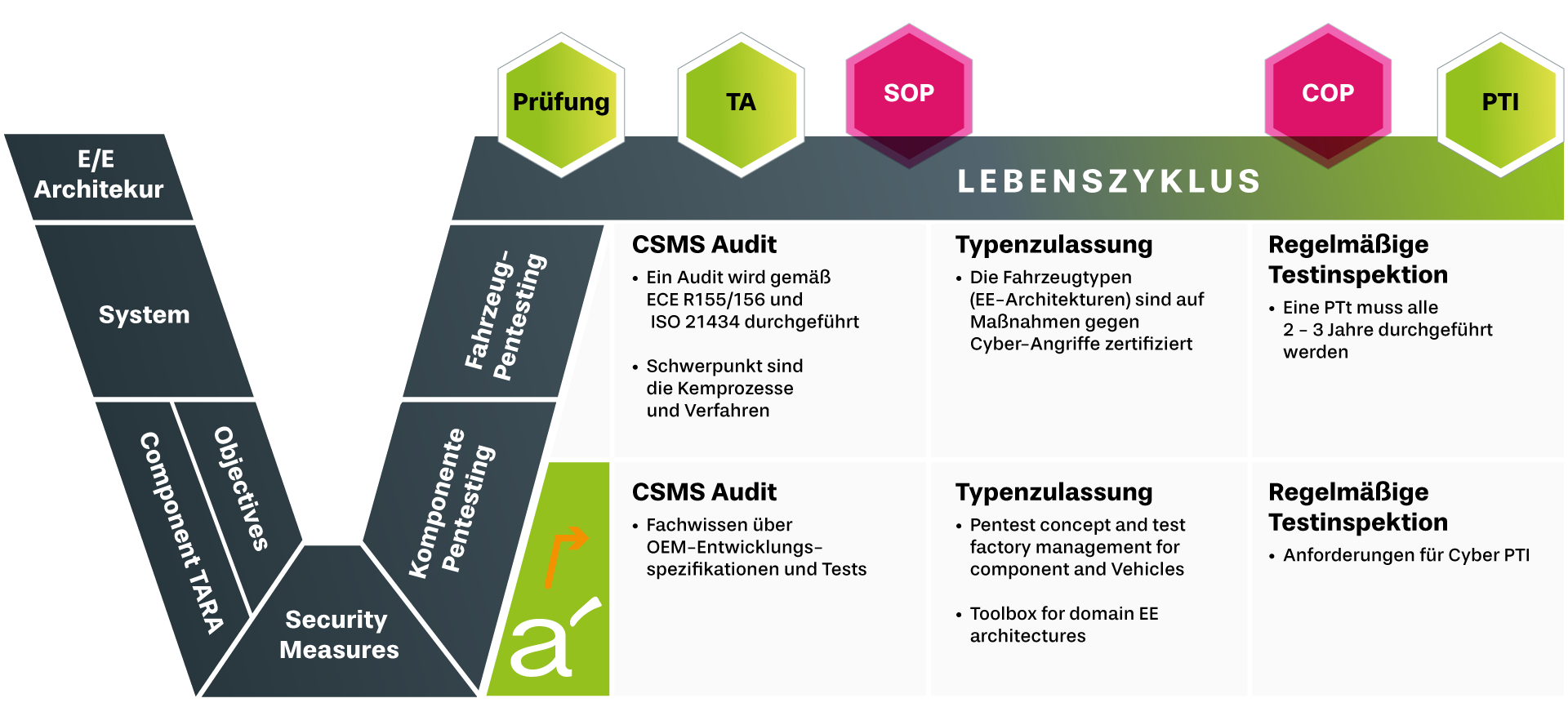
Vehicle Cybersecurity needs to be considered of the lifecyle, this means from development over production and post production and as well from top down over the E/E architecture down to the specific domain ECUs and related SW. Proper automotive Cybersecurity needs prevention, response and testing. The R&D teams focuses on prevention by designing the most secure hardware and software products. Prevention focuses on addressing cybersecurity incidents should they occur and testing is required to ensure reliable products. Modern Vehicle Risk Management needs to consider very different aspects and contexts.

Regulatory Landscape and Process in Automotive Cybersecurity
Automotive cybersecurity regulations such as UN ECE WP.29 R155 (Cybersecurity Management System, CSMS) and R156 (Software Update Management System, SUMS) have been released and are widely adopted across the industry. Additionally, standards such as ISO/SAE 21434 introduce structured cybersecurity risk management processes. These regulations and standards require a more systematic, model-based approach to automotive cybersecurity management.
The process begins with decomposing a vehicle or device into cybersecurity-relevant components. A vulnerability and risk assessment is then conducted on these components to identify potential threats. Based on the assessment, preventive measures are implemented to mitigate risks and enhance overall cybersecurity resilience.

How to comply with UN ECE Regulation?
UN CYBERSECURITY REGULATION