Why effective risk management requires different perspectives
Imagine two people walking in opposite directions on a circular track. Eventually, they’ll meet—because no matter where they start, the path leads to the same point.
This metaphor fits perfectly when we talk about cybersecurity in IT and OT environments. At first glance, these two worlds seem to have very different priorities and approaches. But when it comes to cybersecurity, they’re aiming for the same thing: effective cyber risk management.
What makes all the difference is how risks are assessed and prioritized in each domain.
Same formula – different variables
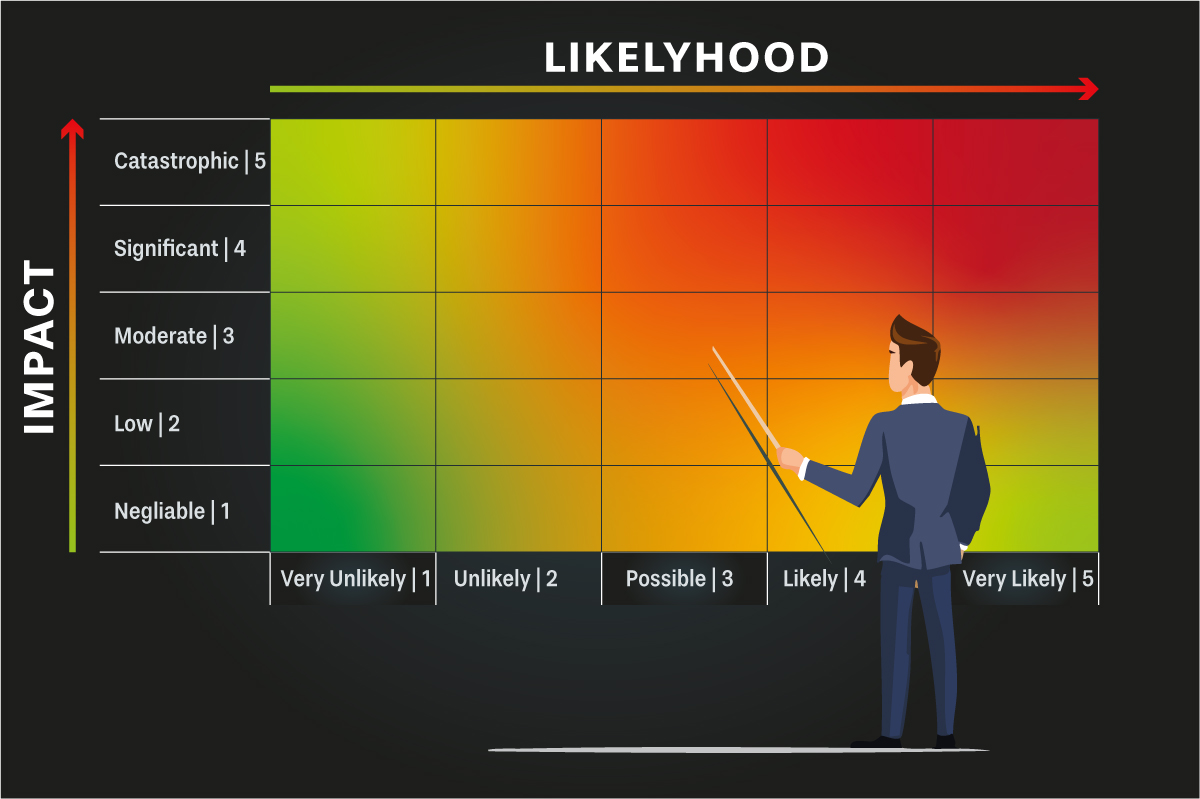
Simplified risk matrix for presenting cyber risks in the context of a risk assessment.
Whether in IT or OT:
Risk is often calculated using the formula
Risk = Impact × Likelihood
But here’s the catch: The way we evaluate impact and likelihood in IT environments differs significantly from OT systems.
OT: Physical processes, long lifecycles, high availability
In OT environments (Operational Technology), cyber risk assessment must consider unique factors:
Impact in OT
IT: Data protection, reputation, and compliance
In IT environments, the focus shifts significantly:





