Maybe you have heard by now about the Cloud and the Edge? Both refer to computation and computers, but the Cloud refers to a large set of computers that are in continuous connection with a device. It is always on and updates all the time. The edge means that data from the device is stored locally – either on the device or on a router somewhere. It updates to the Cloud every ten minutes, every hour, every day. Talk about these two has been going on for a few years now, but this was a situation common in the middle of the last century. Take a factory for example. Machines would collect data about their performance and store them locally. They stayed in an intra-net and never left that factory. A typical case of edge computing. Also, a quiet secure way of doing things as there was no interference from outside and nothing going out neither.
This changed with the internet. Three broad movements in business, manufacturing and computing led to the coining of the term Internet of Things, by Kevin Ashton, in 1999. The first was named pervasive computing and IBM promoted this as a term to describe how things would start to interconnect and create a kind of talking planet. The second movement was spearheaded by Xerox Parc’s Marc Weiser (do take a little time to read his wonderful and visionary core paper) who started from the end-users’ perspective and wondered why – in the nineties of last century- people were still using a mouse and a keyboard (familiar?) to interact with a connected home, car, street, city, instead of much more intuitive ways of doing that. He foreshadowed with the term ubicomp what is now termed the Metaverse, an environment in which through AR and VR you interact through avatars or movement, or gestures. And the third was termed Ambient Intelligence by Philips. They pioneered in real business cases especially in the medical world. None of these terms made it to the general world as they were coined by individual business others did not want to become entangled in their ecosystem. Along came a product manager from Proctor and Gamble with the oh so logical term Internet of Things. Every year people think well now this year is surely the end of IoT as a productive term but no, it persists and is still very live today, more than twenty years after it was conceived.
The reason is that the IoT describes such a huge, radical, and fast change that most people have not even begun to understand what is happening. The internet and the internet of things change every procedure that is in place after five hundred years after the last ontological – read: massively deep – change in data and information: the book. It was technically possible to create books in 1452, yet most public libraries in Europe stem from early 19th century. A mix of negative – censorship, and positive – education arguments led to a dynamic ecosystem in which it took about 400 to 500 years for citizens to be fully on par with government and business ecosystems. In comes the internet. Its protocol says pass on the packet. There are no gatekeepers, there is no diploma that you need, there is no security, just flow and speed, the two things that normally would take hundreds of years of careful top-down management.
Yet all tools in and of society are still tuned to the relatively stable book period. It is only now that most policymakers are beginning to see how fundamental the changes are by talking about Society 5.0, which is a step from Industry 4.0 when policies were set to start regulating the huge data ecosystems in private hands.
The result of this slow response is augmenting the fragmentation that we feel as citizens, as if there is no longer someone in charge, we are ruled by notifications in our smartphones and so many public capabilities are outsourced that it feels as if Big Tech is in control of the pace of everything. And that pace is just to go faster and faster. Sometimes you just want it to slow down. But we do not want to throw away the proverbial child with the bathwater. The IoT is not just bring more convenience (even if you think it is just more noise) it is an unstoppable move towards bringing transparency to all transactions. Does that sound like 1984? Yes, but only if there are no fundamental changes in the power positions between citizens, big government, and big tech. Is it utopian to believe that such shifts can happen or are already happening? That there is a drive to share data and information on a fundamental level? Let’s have a look at how open source is doing.
Most of the business thought it would not work as open-source software is publicly available code: any person can see, distribute, and modify it at their whim., yet “the total of open-source files changed on Github by UK based contributors in 2020 exceed the 80 million developers with an amazing +33% YoY growth. There are more metrics that prove the great increase of open-source contribution in the UK, which suggests the big surge of Open source contribution overall, especially when comparing with years such as 2005, when, allegedly, it was difficult as a developer to work in a company where the developed software system was based on open source.”[1] Nowadays integrating open-source technologies and tools in businesses “is not an option anymore but a necessity.”[2]
Especially when it comes down to security: “What do you trust more? Security in a product that is fully transparent, where you have tens or hundreds of workers across the world testing and working on it, as opposed to a product where you have not seen the source at all.” [3] This growing success has led to new areas of business like SCA, software component analysis as “manual tracking of open source code is no longer sufficient; it simply can’t keep up with the sheer amount of open source. And the increasing prevalence of cloud-native applications and more-complex applications make robust and dependable SCA tools a necessity.”[4] (SCA) is an automated process that identifies the open-source software in a codebase. This analysis is performed to evaluate security, license compliance, and code quality.”
IoT is suffering from increasing cybersecurity problems caused by software vulnerabilities. In 2020 the malware infection of IoT devices raised 100%, causing 33% of malicious activities in networks, and vulnerable software is the main reason for this mess.
Software stacks in IoT are often built upon software supply chains, including multiple sources. Users need a clear picture of all software installed to improve IoT device security. This goal will be reached through a Software-Bill-of-Materials, which documents all installed software. However, many IoT products such as connected cars are built-in highly complex supply chains with n-tier suppliers. The software base will continuously change by over the air updates. Current centralized systems for a bill of material cannot map the requirements towards security and confidentially needed for trusted data exchange: centralized architectures
[1] https://hackernoon.com/why-open-source-conquers-the-telecommunications-industry-121i33l3
[2] https://analyticsindiamag.com/trends-that-defined-open-source-this-year/
— from the Dev Interrupted Podcast at 8:20
https://devinterrupted.com/benefits-of-open-source-in-your-organization/
[4] https://www.synopsys.com/glossary/what-is-software-composition-analysis.html
are less flexible and a single point of failure. The result is a lack of information and trust in provided data.
Security along these lines becomes more than a defensive attitude, it becomes a proactive engagement. As one of the SCA companies, asvin.io feels it becomes much more an issue of Trust. Asvin.io aligns the following workstreams to cover the 3 dimensions of software supply chain risk management to create a real time model for risk scoring, which can be accessed by automated API by suppliers, OEM and 3rd Parties (as regulators or insurance industry):
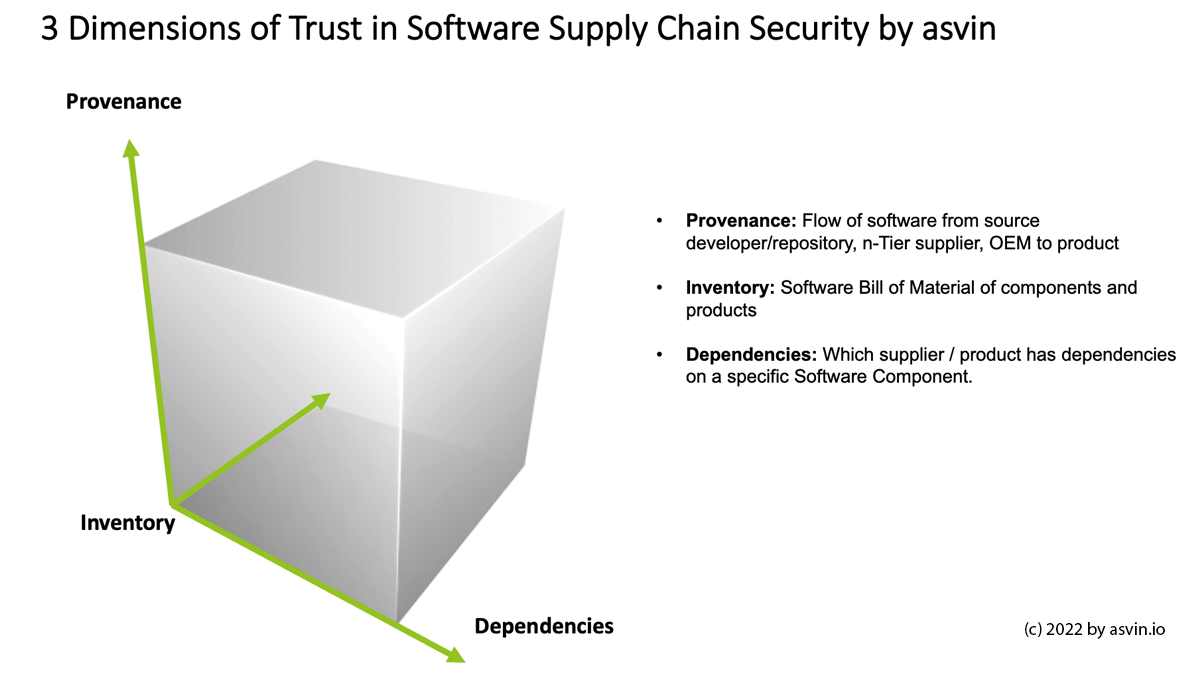
Dimension A: Provenance: Track and Trace the Software Lifecycle of a component from n-supplier towards OEM
Dimension B: Inventory: Distributed Sofware Bills of Materials D-SBOM – Provide a shared / distributed network for suppliers to submit their SBOM towards the actors in the supply network
Dimension C: Dependencies – Provide Datapoints / Markers to identify dependencies of a specific component / supplier in the network: e.g. component is used at OEM a and OEM b
D-SBOM (Distributed Software Bills of Material) will provide a solution in complex IoT software supply chains to document all the software used in IoT devices and distribute this information in a secure and trusted way towards all users and actors.
“With D-SBOM, IoT vendors can keep track of the software installed on IoT devices and their origin. The information will enable operators to continuously monitor IoT devices on known software vulnerabilities (CVE) and plan their risk mitigation as updating or isolating devices. Using blockchain and DLT, D-SBOM will provide a novel solution, which is more secure and advanced than existing centralized models:
- Immutable storage of information, protected from manipulation by cyberattacks
- Increased trust by consensus mechanism in the software supply chain
- Protocols using open-source stacks of Hyperledger and Ethereum Foundation”[5]
Gartner estimates fewer than 50% of organizations have adopted SCA tools, “although adoption will continue to increase steadily, given new market drivers. Some of the key drivers for adopting SCA, are requirements for software bill of materials (SBOM) and enhanced OSS governance.”[6] The Software Composition Analysis (SCA) Software market will rise at a considerable rate during the the period, 2022 to 2029. “In 2022, the market is growing at a steady rate and with the rising adoption of strategies by key players, the market is expected to rise over the projected horizon.”[7]
Founded in September 2018, Stuttgart-based asvin GmbH provides a platform-as-secure-solution based on Distributed Ledger Technology (DLT) for managing the software product life cycles associated with networked devices used in the Internet of Things. The applications and services support trace software, enable secure Over-the-Air updates and detect security vulnerabilities in IoT and IIoT to mitigate risk and ensure uninterrupted business processes.. asvin has been awared as Best Cybersecurity Startup – EUROPE 2022 by the Cybersecurity Excellence Award. The Cybersecurity Excellence Awards is an annual competition honoring individuals and companies that demonstrate excellence, innovation and leadership in information security.
“At asvin we are convinced that decentralized technologies will enhance the resilience of cybersecurity in the Internet of Things. Distributed Ledgers are an important building block building defense technology layers for preventing malicious cyberattacks on the software supply chain in critical infrastructures and industries. We are looking forward to introducing strong decentralized solutions for cybersecurity in the automotive supply chain and car software lifecycle.” – Mirko Ross, CEO, asvin
In an earlier interview Ross speaks of educating the full work force and not only leaving cybersecurity to the team of hackers and experts responsible for it. The best line of defense is a that everyone in the company has basic cybersecurity skills and awareness. Therefore asvin.io is partner of the #IoTDay. IoT Day and is an open invitation to the Internet of Things Community to set up an event, a lunch, a talk with the neighborhood on what #IoT is and what it means in everyday life for all of us. It has been ongoing for over a decade and has facilitated and cheered on over 500 events worldwide. These events are self-organized and reach into communities where the regular conferences and meetings cannot reach to start a debate and let people be heard on what kind of connectivity they would want for their homes, their cars, their health, and their streets. See for example this event in Paris.[8]
You are very welcome to add one of your own. Maybe you have a good way to explain the cloud and the edge?
Go
[5] https://www.trublo.eu/d-sbom/
[6] https://www.whitesourcesoftware.com/resources/research-reports/gartner-2021-market-guide-for-software-composition-analysis/
[7] https://www.newschannelnebraska.com/story/45698393/software-composition-analysis-(sca)-software-professional-market-2022-global-share-growth-size-opportunities-trends-regional-overview-leading-company-analysis-and-key-country-forecast-to-2029
[8] https://www.journaldunet.com/ebusiness/internet-mobile/1509425-maurice-zembra-vertical-m2m/
About the Author:
Rob van Kranenburg
 |
LinkedIn: https://www.linkedin.com/in/robvankranenburg/
Twitter: https://twitter.com/robvank |
As the Founder of the Internet of Things Council (2009) and IoT Day (2010) Rob has acquired the expertise to co- explore new innovation pathways with the team of asvin GmbH and enlarge the already impressive ecosystem. His long standing experience and publications in the field of Internet of Things, Industry 4.0 and ‚total‘ connectivity in the space of flows offers him the perfect background to develop innovation strategies for the use cases of our technology and to co-create with the team quick wins and long term gains. Rob lives in Gent, Belgium. In his free time, he is an avid reader of (German) poetry. He is interested in the sovereign identity debate and the concept of disposable identities. Rob joined asvin 2022 as Chief Innovation Officer (CIO).





