
Effective cybersecurity is the result of data-sovereign actors.
Digital Sovereignty – from risk to advantage: How cybersecurity and data sovereignty accelerate your business success.
A plea for data-driven OT resilience.
OT can usually only be patched to a limited extent, if at all – but it can be matched! This means that manufacturing companies can now also operate their production facilities in a cyber-secure manner with a software mix of graph analysis, topology theory and AI. And that’s not all. It also enables them to act with data sovereignty in an increasingly monopolised and unprotected cyber space. Here’s how.
Cyber security in manufacturing is like squaring the circle, because OT cannot be protected with simple IT measures. Manufacturing machines, such as outdated SCADA systems, cannot be patched. They can only be protected by securing their network environment, for example through network segmentation or environment monitoring. asvin has developed a software platform for this problem that turns unstructured environment parameters into computable Cyber Threat Intelligence data, making security measures recognisable, describable and prioritiseable.
Reverse thrust: Manufacturers are becoming cyber creators instead of cyber victims
This approach enables manufacturing companies to achieve digital sovereignty in several ways. They can plan, set up and operate the cyber security of their systems more easily than ever before. Attackers fail due to the increasingly stable resilience of their supposed victims. Last but not least, monopolistic BigTechs are faced with users and customers who are increasingly confident in paying attention to contract terms, dependencies and legal violations. And, as in Denmark, Australia and Schleswig-Holstein, they are initiating the replacement of large platform providers.
asvin Software separates the wheat from the chaff
In a situation like this, where there is a lot of speculation, obfuscation and downplaying about cyber security and digital sovereignty, or where ignorance is accepted, clarity and an overview of the actual conditions prevailing in cyberspace are essential. From our point of view, cyber transparency is therefore as valuable as the resource data itself.
Resilience tools for sovereign actors
Without automated risk analysis, there can be no optimised digital processes for type approval of vehicles or, more generally, for the transformation of the automotive and manufacturing industries towards new production technologies and diversified business models. Without protection of LLM training data, there can be no unique selling point for the use of AI in machine tool manufacturing. And without cybersecurity by design, there can be no regulation-compliant, secure products with digital elements in accordance with the EU Cyber Resilience Act.
Data-driven, automated threat detection
The basis for transformative cybersecurity lies in asvin’s Risk by Context™ technology. With Risk by Context™, we provide a dynamic risk management tool that can be adapted to individual requirements. It is based on AI-based cybersecurity knowledge graphs and graph neural networks (GNN), both of which generate structured and actionable Cyber Threat Intelligence (CTI) data from unstructured environmental parameters. This allows threats in industrial networks to be assessed and prioritised not only statically, but also in context. The software prioritises risks not only according to cyber threats, but also according to health, safety and environment (HSE) criteria. Example: A hacked robot with potential danger to employees is rated higher than a pure IT vulnerability. Overall, manufacturing companies can now deploy their resources in a targeted manner and efficiently manage their investments in cyber security.
Independence from hyperscalers
All asvin solutions are designed to meet European and German standards. This reduces dependence on global cloud providers and ensures that sensitive production data is protected within the European legal framework. This enables companies to manage their cyber security risks in a legally compliant manner, maintain control over software and data flows, and operate independently of external, global providers. This strengthens the resilience, trustworthiness and competitiveness of manufacturing in Europe.
Comparison table:


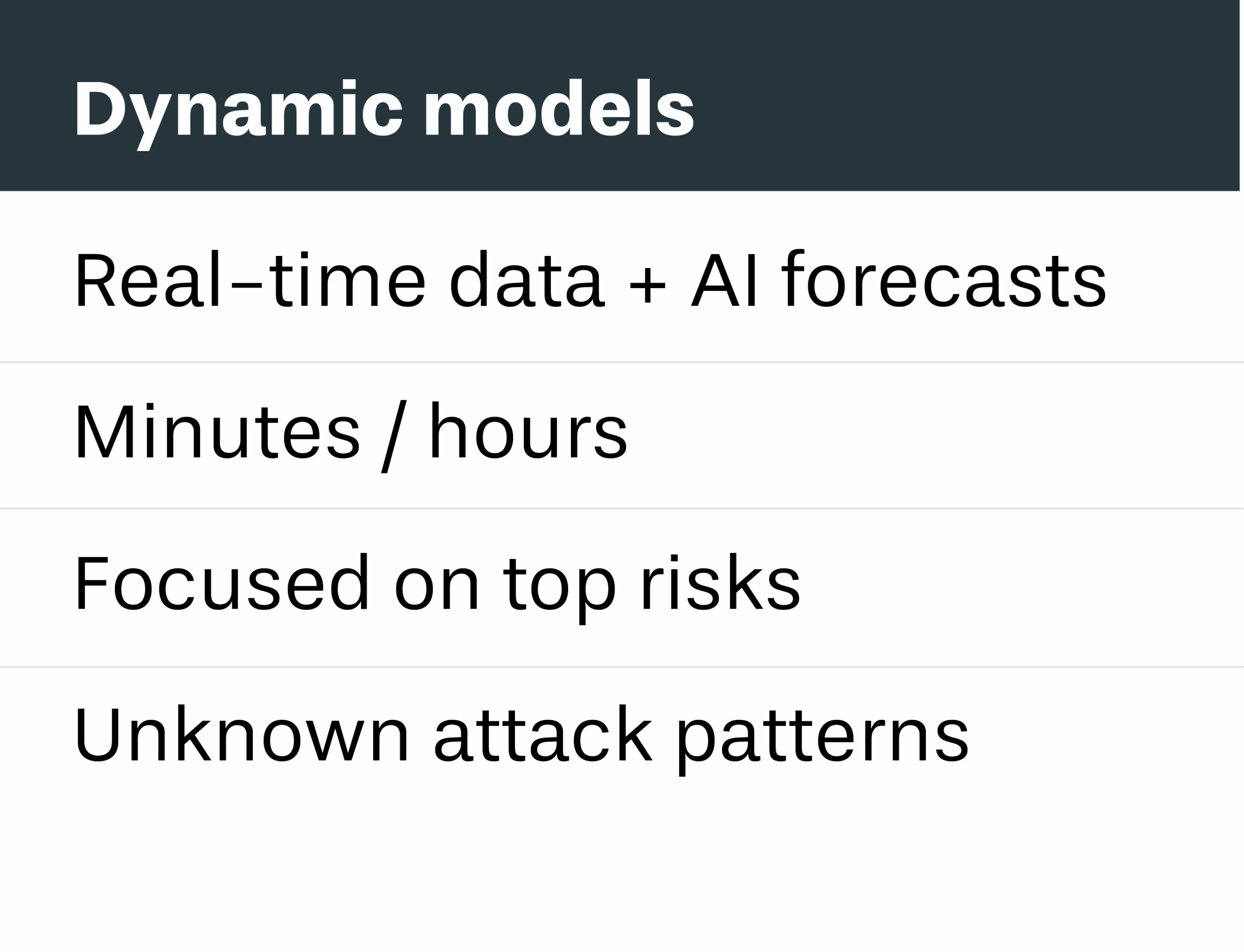
Comparison: Dynamic vs. static


A few notes on the technology behind Risk by Context™
Customers populate our tool with the information that is particularly important for their cyber risk assessment. This initially includes data on network topology, business criticality, user roles, HSE index or CVSS score from an asset management system. Location data and other specific information are also added. We use Angular with Typescript as our front-end technology framework, .NET in the back-end, and the JSON database mongodb and the graph database neo4j as our database. We support OT asset management systems such as OTbase, Nazomi and Siemens OT Companion. The product is delivered via Docker images running on a Kubernetes cluster in our cloud. All APIs are secured with Jason Web Token as an access token. We use OAuth 2.0 for our own identity management solution. Further details on implementation, customisation and operation are available on request.






