The core principle of asvin IoT update firmware platform is to extend and maintain security of IoT devices. Along these lines, we have implemented and integrated the latest developments in the area of cryptography to the asvin BeeHive over the air update solution. One of the objectives of Fed4FIRE+ experiment was to evaluate the cryptographic encryption algorithms such as Homomorphic Encryption (HE), Functional Encryption (FE), and Physically Unclonable Functions (PUF). As part of the iterative experiments we have collected the results for these encryptions. We have positive results and some areas of improvement to share.
Homomorphic Encryption
Homomorphic encryption (HE) is a type of encryption that allows one to perform operations and process encrypted data without prior decryption of it. The output of these operations is in encrypted form and when it is decrypted the output is same as if the operations were performed on unencrypted data. This encryption is very useful in applications where privacy is of utmost importance. E.g., consider a use case where certain algorithms are to be run on an external cloud service on a company’s financial data. This problem when approached with classical methods, the data must be decrypted first thus involving data privacy-based vulnerabilities. In this case, the homomorphic approaches are useful.
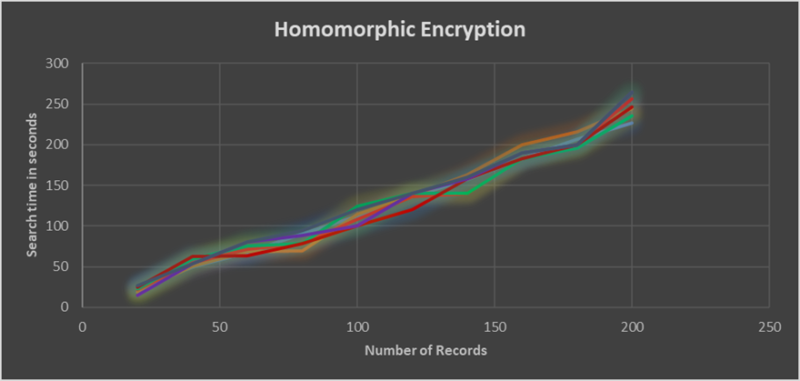
While homomorphic encryption has promising application for future, in its current state it is quite slow to serve real world use cases. For the Fed4FIRE experiment, we created a small data sample of device and firmware Ids. In the asvin BeeHive patch distribution platform, device and firmware ids are used to manage the IoT devices and performa rollouts. The idea was to perform search operation using the HE on the data samples and monitor the time taken by the operation. The small data samples with 23 devices returned output in approximately 30 seconds which, compared to conventional search on unencrypted data is slower by many magnitudes. The search time increases significantly with number of records in the database. The below figure illustrates that the search time increases with number of records in database.
Functional Encryption
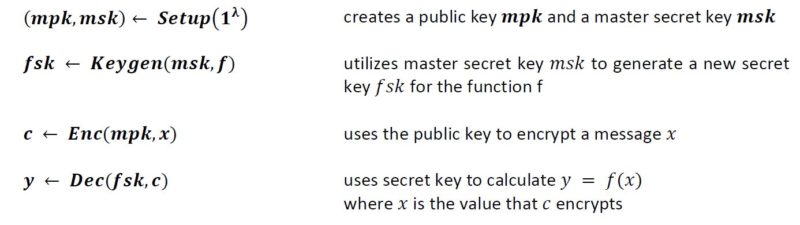
Functional encryption (FE) is a public key encryption scheme in which specific functions can be performed on encrypted data without revealing the actual data. It can be defined more formerly with the following mathematical algorithms.
For the experiment, we created a small program of to calculate vector product of random vectors using single input scheme. The code and details of the program are published in our GitHub repo.
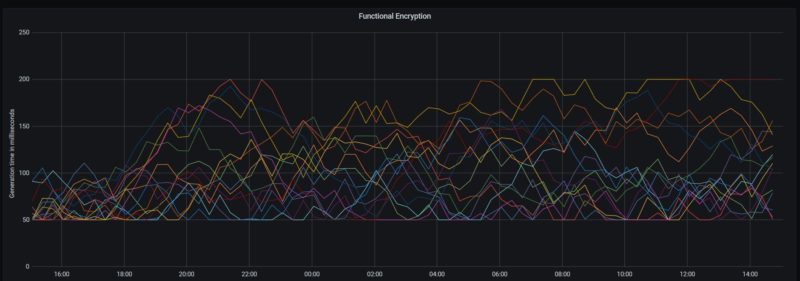
Currently, the functional encryption supports only vector multiplication and quadratic polynomial functions. These functions are good to demonstrate its use case. The figure below represents the generation time of Functional Encryption. But it is far from a real-world use case. A practical scenario requires a function to be more sophisticated. For an example search query, data manipulations in database, other sophisticated computational tasks.
Physically Unclonable Function
Physically Unclonable Function (PUF) is a physical entity incorporated in a physical structure. PUF takes advantage of the inherent submicron variations that occur naturally during semiconductor fabrication. These variations are length, width, thickness etc. This results in variation in electrical properties thus creating a unique identity. In our experiment, we used SRAM based PUF. In this case, each time when the SRAM block powers on, the cells could be either a 1 or 0. The figure below shows the working principle of PUF.
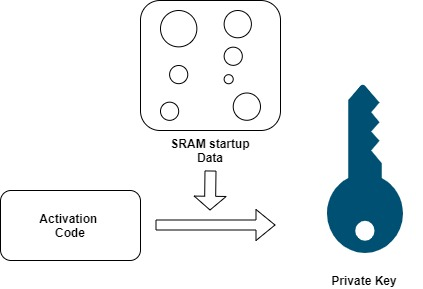
These random cell values result in random and repeatable patterns, which is unique to each chip. This is called as SRAM startup Data. This SRAM Startup Data along with the Activation Code are turned into digital fingerprint used as secret key that is used while communication with the webserver. You can find more details about hardware/software setups and generation procedure in our series of blogs on PUF. The board is also used to encrypt and decrypt plain text which is depicted in the figure below.
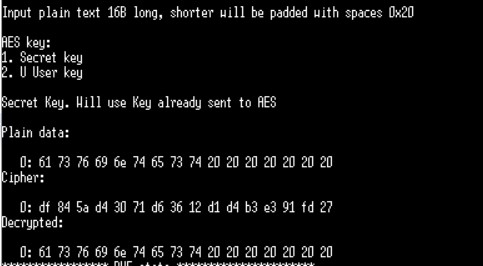
Physically Unclonable Function solution is reliable, and we are going to integrate it in asvin BeeHive over-the-air update platform to generate unique Id for IoT devices and also use as encryption keys. The PUF based cryptographic solution is a big value addition to the security feature of the IoT devices.
Conclusion
Under the Fed+FIRE+ stage 2 experiment, performance and feasibility studies of HE, FE and PUF were done. All the encryption algorithms has great potential to disrupt and revolutions security of digital services. The HE and FE are not very useful for asvin platform in the present form. We will keep an eye on the progress of these encryptions. Finally, the PUF based ID for IoT devices is very promising and we will integrate this solution to asvin framework. This is final blog in our series of blogs on results of Fed4FIRE+ stage 2 experiment.
Start with asvin Register now





