Wikipedia ” A physical unclonable function or PUF, is a physical object that for a given input and conditions (challenge), provides a physically-defined “digital fingerprint” output that serves as a unique identifier ”
This is the first in our series of blog posts on the Physical Unclonable Function (PUF) where we will explore PUF technology, the generation of PUF keys and finally share a Use Case demonstrating the benefits of PUF as a component of the asvin platform.
PUF has infinite application possibilities but in this series we will focus on Static Random Access Memory or SRAM-based PUF.
Introduction:
PUF takes advantage of submicron variations that occur naturally during semiconductor fabrication. These variations occur in the physical parameters such as length, width, thickness, etc of semiconductor materials. Such material property variations result in electrical properties which are not completely controllable making them very difficult to replicate but ideal for generating a unique, identifying ‘fingerprint’ for the devices where the semiconductor is housed.
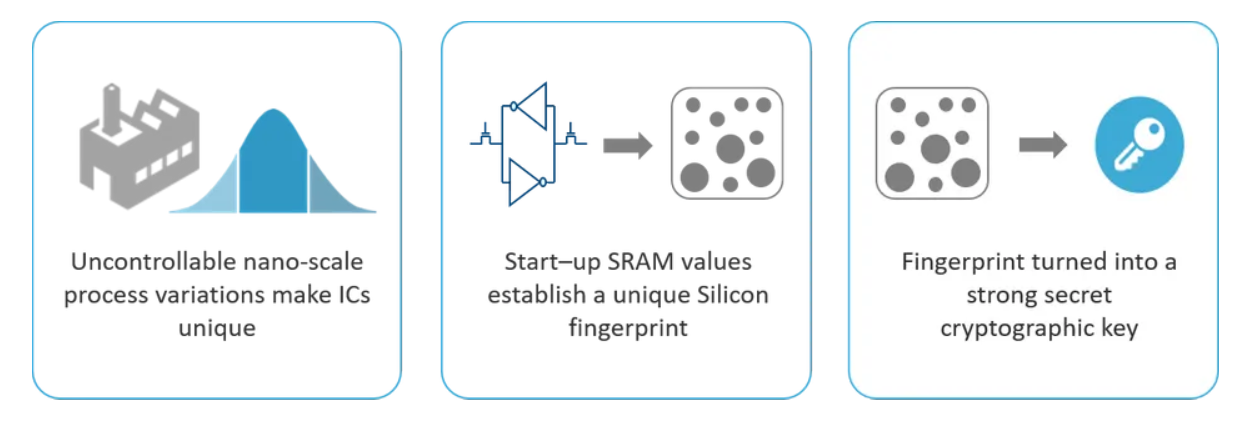
(source: www.intrinsic-id.com )
The figure above demonstrates SRAM-based PUFs. In this example, because of the organic variations, when the SRAM block powers-on the cells could be either a 1 or 0. These cell values, unique to each chip, result in random but repeatable patterns that are referred to as SRAM Startup Data. This SRAM Startup Data in combination with an Activation Code becomes a digital fingerprint used for encryption keys and unique ID for further applications.
PUF Security:
Devices where keys stored in flash or other memory regions are susceptible to hacking. Chip decapping can be used to read the entire memory of a device and then extract its critical keys and secrets posing a threat for the device ecosystem and potentially leading to a data breach in the IoT network.
In the case of PUF-based keys each device has a unique digital fingerprint and since the fingerprint is not saved on its associate chip it cannot be read. The unique device fingerprint is generated only when the device is turned on and the activation code is paired to it. This makes PUF-based devices resilient to a decapping attack.
Applications:
Having been successfully tested against disruptive influences such noise, repeatability and aging PUF-based IC’s are now commercially available. The deployment of PUF-based security applications are picking up pace in the IoT space and IoT device fleets are the perfect environment for PUF-based security. In further blog posts. we will look at a PUF solution from NXP semiconductors and explore the best practices to generate and use PUF-based keys. Stay tuned.
Reference Links:
Intrinsic ID – PUF
NXP – PUF
PUF – The secure silicon fingerprint






