What Security Risks Await in the Factory Automation Cyber Landscape?
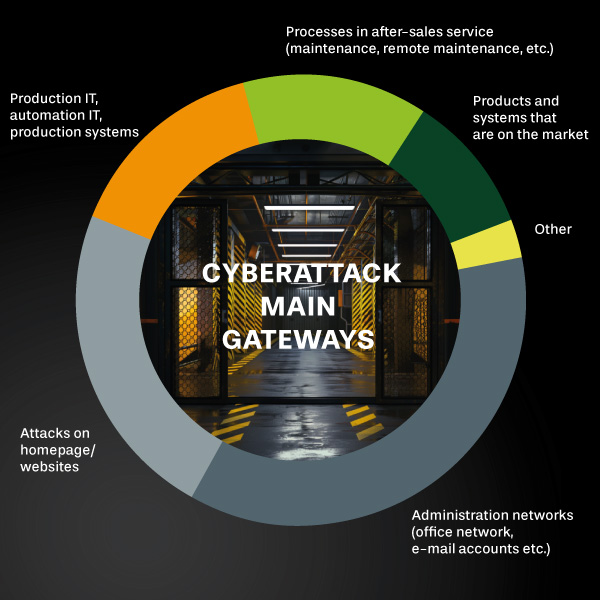
In the Industry 4.0 era, ensuring the OT security of your manufacturing operations during digital transformation is crucial. With many industrial plants installed before cybersecurity became a priority, vulnerability to external threats has heightened. As manufacturing processes grow more interconnected, the risk of cyber breaches increases, especially with outdated systems lacking modern security features. Unlike IT systems, OT environments pose unique challenges where applying patches can disrupt operational assets or require waiting until the next maintenance cycle to minimize disruptions.
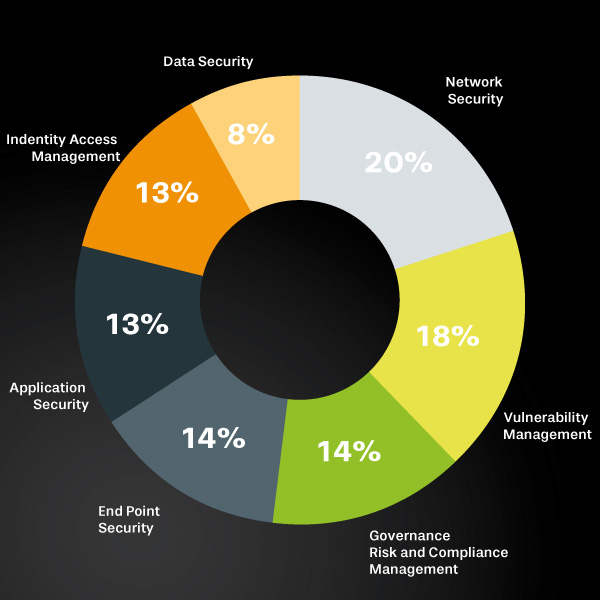
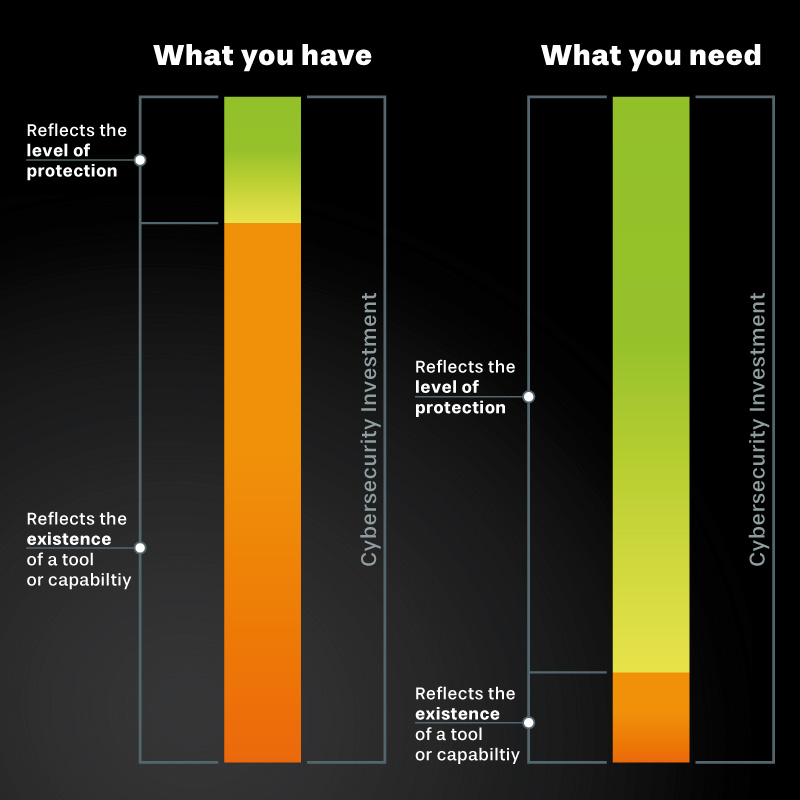
What can asvin do to help me secure my assets and avoid downtime?
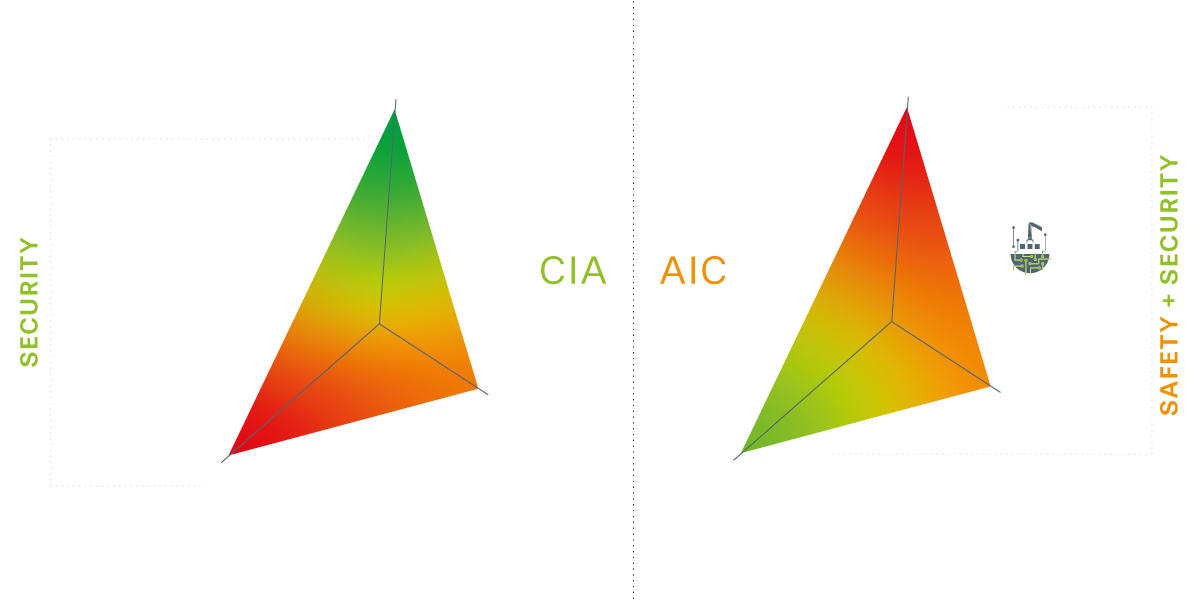
In IT, the three main security objectives are Confidentiality, Integrity, and Availability (CIA). In OT, Availability takes precedence over Integrity and Confidentiality (AIC). It’s crucial to balance IT and OT security to ensure a successful security strategy that meets specific requirements and priorities.